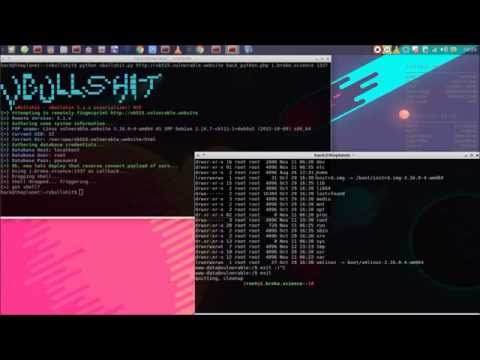
This is an exploit for the PHP Object Injection vulnerability recently disclosed in the reasonably popular vBulletin forum software. Our exploit does some basic information gathering before firing off the usual payload to give us a reverse connecting PTY shell. Currently, we only have a Python payload available, but that might change sometime.
You just need to specify the target, payload, and callback host/port. Example use is outlined in the video below.
Licenced under the WTFPL