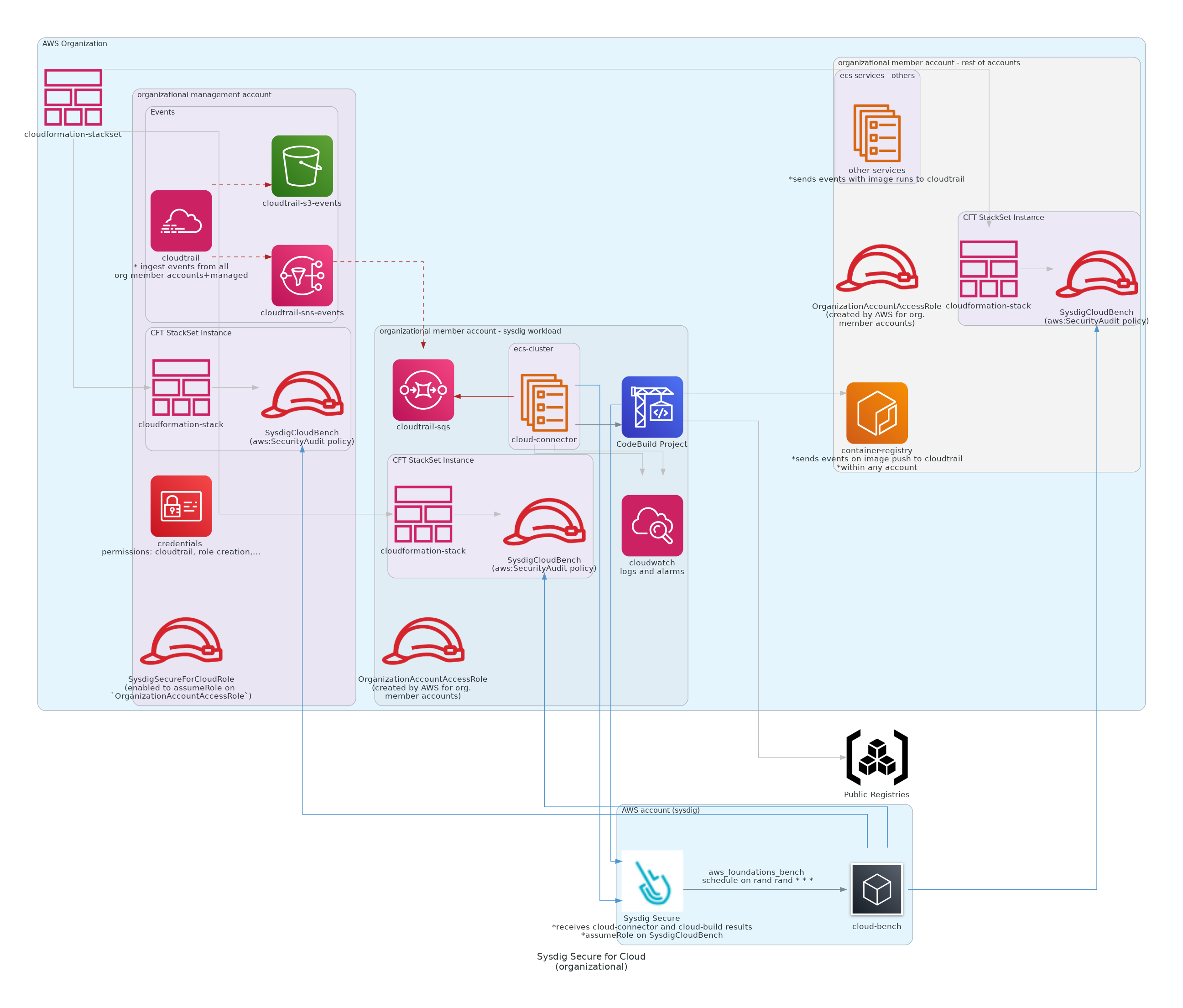
Assess the security of your organization.
Deploy Sysdig Secure for Cloud using an AWS Organizational Cloudtrail that will fetch events from all organization member accounts (and the managed one too).
- In the management account
- An Organizational Cloutrail will be deployed (with required S3,SNS)
- An additional role
SysdigSecureForCloudRolewill be created- to be able to read cloudtrail-s3 bucket events (and query cloudtrail-sqs) from sysdig workload member account.
- scanning-only, to assumeRole over member-account role
- to scan images pushed to ECR's that may be present in other member accounts.
- to describe ECS task definitions and get images to be scanned, on clusters in other member accounts
- In the user-provided member account
- All the Sysdig Secure for Cloud service-related resources/workload will be created
- All Sysdig Secure for Cloud features but Image Scanning are enabled by default. You can enable it through
deploy_image_scanning_ecranddeploy_image_scanning_ecsinput variable parameters. - Resource creation inventory Find all the resources created by Sysdig examples in the resource-group
sysdig-secure-for-cloud(AWS Resource Group & Tag Editor) - Deployment cost This example will create resources that cost money.
Runterraform destroywhen you don't need them anymore - For free subscription users, beware that this example may not deploy properly due to the 1 cloud-account limitation. Open an Issue so we can help you here!
Minimum requirements:
-
Have an existing AWS account as the organization management account
- Within the Organization, following services must be enabled (Organization > Services)
- Organizational CloudTrail
- Organizational CloudFormation StackSets
- Within the Organization, following services must be enabled (Organization > Services)
-
Configure Terraform AWS Provider for the
managementaccount of the organization- This provider credentials must be able to manage cloudtrail creation
You must be logged in with the management account for the organization to create an organization trail. You must also have sufficient permissions for the IAM user or role in the management account to successfully create an organization trail.
- This provider credentials must be able to manage cloudtrail creation
-
Organizational Multi-Account Setup, ONLY IF SCANNING feature is activated, a specific role is required, to enable Sysdig to impersonate on organization member-accounts and provide
- The ability to pull ECR hosted images when they're allocated in a different account
- The ability to query the ECS tasks that are allocated in different account, in order to fetch the image to be scanned
- By default, it uses AWS created default role
OrganizationAccountAccessRole- When an account is created within an organization, AWS will create an
OrganizationAccountAccessRolefor account management, which Sysdig Secure for Cloud will use for member-account provisioning and role assuming. - However, when the account is invited into the organization, it's required to create the role manually
You have to do this manually, as shown in the following procedure. This essentially duplicates the role automatically set up for created accounts. We recommend that you use the same name, OrganizationAccountAccessRole, for your manually created roles for consistency and ease of remembering.
- If role name,
OrganizationAccountAccessRolewants to be modified, it must be done both on theawsmember-account provider AND input valueorganizational_member_default_admin_role
- When an account is created within an organization, AWS will create an
-
Provide a member account ID for Sysdig Secure for Cloud workload to be deployed. Our recommendation is for this account to be empty, so that deployed resources are not mixed up with your workload. This input must be provided as terraform required input value
sysdig_secure_for_cloud_member_account_id=<ORGANIZATIONAL_SECURE_FOR_CLOUD_ACCOUNT_ID> -
Sysdig Secure requirements, as input variable value with the
api-tokensysdig_secure_api_token=<SECURE_API_TOKEN>
Role usage for this example comes as follows. Check permissions too
-
management account
- terraform aws provider: default
SysdigSecureForCloudRolewill be created- used by Sysdig to subscribe to cloudtrail events
- used by Sysdig, for image scanning feature, to
assumeRoleonOrganizationAccountAccessRoleto be able to fetch image data from ECS Tasks and scan ECR hosted images
SysdigCloudBenchrole will be created for SecurityAudit read-only purpose, used by Sysdig to benchmark
-
member accounts
- terraform aws provider: 'member' aliased
- this provider can be configured as desired, we just provide a default option
- by default, we suggest using an assumeRole to the AWS created default role
OrganizationAccountAccessRole- if this role does not exist provide input var
organizational_member_default_admin_rolewith the role
- if this role does not exist provide input var
SysdigCloudBenchrole will be created for SecurityAudit read-only purpose, used by Sysdig to benchmark
- terraform aws provider: 'member' aliased
-
sysdig workload member account
- if ECS workload is deployed,
ECSTaskRolewill be used to define its permissions- used by Sysdig to assumeRole on management account
SysdigSecureForCloudRoleand other organizationsOrganizationAccountAccessRole
- used by Sysdig to assumeRole on management account
- if ECS workload is deployed,
For quick testing, use this snippet on your terraform files
terraform {
required_providers {
sysdig = {
source = "sysdiglabs/sysdig"
configuration_aliases = [aws.member]
}
}
}
provider "sysdig" {
sysdig_secure_url = "<SYSDIG_SECURE_URL>"
sysdig_secure_api_token = "<SYSDIG_SECURE_API_TOKEN>"
}
provider "aws" {
region = "<AWS_REGION> # same region in both providers. ex. us-east-1"
}
provider "aws" {
alias = "member"
region = "<AWS_REGION> # same region in both providers. ex. us-east-1"
assume_role {
# 'OrganizationAccountAccessRole' is the default role created by AWS for managed-account users to be able to admin member accounts.
# <br/>https://docs.aws.amazon.com/organizations/latest/userguide/orgs_manage_accounts_access.html
role_arn = "arn:aws:iam::${var.sysdig_secure_for_cloud_member_account_id}:role/OrganizationAccountAccessRole"
}
}
module "secure_for_cloud_organizational" {
providers = {
aws.member = aws.member
}
source = "sysdiglabs/secure-for-cloud/aws//examples/organizational"
}See inputs summary or module variables.tf file for more optional configuration.
To run this example you need have your aws management-account profile configured in CLI and to execute:
$ terraform init
$ terraform plan
$ terraform apply| Name | Version |
|---|---|
| terraform | >= 1.0.0 |
| aws | >= 4.0.0 |
| sysdig | >= 0.5.33 |
| Name | Version |
|---|---|
| aws | 4.26.0 |
| aws.member | 4.26.0 |
| sysdig | 0.5.39 |
| Name | Source | Version |
|---|---|---|
| cloud_bench | ../../modules/services/cloud-bench | n/a |
| cloud_connector | ../../modules/services/cloud-connector-ecs | n/a |
| cloudtrail | ../../modules/infrastructure/cloudtrail | n/a |
| codebuild | ../../modules/infrastructure/codebuild | n/a |
| ecs_vpc | ../../modules/infrastructure/ecs-vpc | n/a |
| resource_group | ../../modules/infrastructure/resource-group | n/a |
| resource_group_secure_for_cloud_member | ../../modules/infrastructure/resource-group | n/a |
| secure_for_cloud_role | ../../modules/infrastructure/permissions/org-role-ecs | n/a |
| ssm | ../../modules/infrastructure/ssm | n/a |
| Name | Type |
|---|---|
| aws_iam_role.connector_ecs_task | resource |
| aws_caller_identity.me | data source |
| aws_iam_policy_document.task_assume_role | data source |
| aws_region.current | data source |
| sysdig_secure_connection.current | data source |
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| sysdig_secure_for_cloud_member_account_id | organizational member account where the secure-for-cloud workload is going to be deployed | string |
n/a | yes |
| benchmark_regions | List of regions in which to run the benchmark. If empty, the task will contain all aws regions by default. | list(string) |
[] |
no |
| cloudtrail_is_multi_region_trail | true/false whether the created cloudtrail will ingest multi-regional events. testing/economization purpose. | bool |
true |
no |
| cloudtrail_kms_enable | true/false whether the created cloudtrail should deliver encrypted events to s3 | bool |
true |
no |
| connector_ecs_task_role_name | Name for the ecs task role. This is only required to resolve cyclic dependency with organizational approach | string |
"organizational-ECSTaskRole" |
no |
| deploy_benchmark | Whether to deploy or not the cloud benchmarking | bool |
true |
no |
| deploy_image_scanning_ecr | true/false whether to deploy the image scanning on ECR pushed images | bool |
false |
no |
| deploy_image_scanning_ecs | true/false whether to deploy the image scanning on ECS running images | bool |
false |
no |
| ecs_cluster_name | Name of a pre-existing ECS (elastic container service) cluster. If defaulted, a new ECS cluster/VPC/Security Group will be created. If specified all three parameters ecs_cluster_name, ecs_vpc_id and ecs_vpc_subnets_private_ids are required. ECS location will/must be within the sysdig_secure_for_cloud_member_account_id parameter accountID |
string |
"create" |
no |
| ecs_task_cpu | Amount of CPU (in CPU units) to reserve for cloud-connector task | string |
"256" |
no |
| ecs_task_memory | Amount of memory (in megabytes) to reserve for cloud-connector task | string |
"512" |
no |
| ecs_vpc_id | ID of the VPC where the workload is to be deployed. If defaulted a new VPC will be created. If specified all three parameters ecs_cluster_name, ecs_vpc_id and ecs_vpc_subnets_private_ids are required |
string |
"create" |
no |
| ecs_vpc_region_azs | List of Availability Zones for ECS VPC creation. e.g.: ["apne1-az1", "apne1-az2"]. If defaulted, two of the default 'aws_availability_zones' datasource will be taken | list(string) |
[] |
no |
| ecs_vpc_subnets_private_ids | List of VPC subnets where workload is to be deployed. If defaulted new subnets will be created within the VPC. A minimum of two subnets is suggested. If specified all three parameters ecs_cluster_name, ecs_vpc_id and ecs_vpc_subnets_private_ids are required. |
list(string) |
[] |
no |
| existing_cloudtrail_config | Optional block. If not set, a new cloudtrail, sns and sqs resources will be created If there's an existing cloudtrail, input mandatory attributes, and one of the 1, 2 or 3 grouped labeled optionals.
|
object({ |
{ |
no |
| name | Name to be assigned to all child resources. A suffix may be added internally when required. Use default value unless you need to install multiple instances | string |
"sfc" |
no |
| organizational_member_default_admin_role | Default role created by AWS for management-account users to be able to admin member accounts. https://docs.aws.amazon.com/organizations/latest/userguide/orgs_manage_accounts_access.html |
string |
"OrganizationAccountAccessRole" |
no |
| tags | sysdig secure-for-cloud tags. always include 'product' default tag for resource-group proper functioning | map(string) |
{ |
no |
No outputs.
Module is maintained and supported by Sysdig.
Apache 2 Licensed. See LICENSE for full details.