Greetings! I'm Lalatendu Swain, a Security Engineer and part-time content creator. I've initiated this repository to provide guidance to aspiring bug bounty hunters. Content will be continually added, so stay tuned and let's embark on this journey together!
Please Note: Bug bounty landscapes have evolved significantly in recent years. The vulnerabilities that were once easily discovered may now pose greater challenges due to increased automation and competition. To succeed in bug bounty hunting, persistence and focus are key.
- Understanding Bugs
- A security bug or vulnerability refers to a flaw in software or hardware that, when exploited, compromises confidentiality, integrity, or availability.
- Exploring Bug Bounties
- Bug bounty programs offer rewards for discovering and reporting bugs in software products, fostering improvement and user engagement. Rewards vary based on severity and may include monetary compensation, subscriptions, discounts, or swag items.
- Technical Skills
- Computer Fundamentals
- Computer Networking
- Operating Systems
- Programming
- C Programming
- Python Programming
- JavaScript
- PHP
- Books
- Writeups
- Forums
- Official Websites
Connect with top security researchers and bug bounty hunters on Twitter. Stay updated on new issues, vulnerabilities, and methodologies shared by experts in the cybersecurity field!
- Capture The Flag (CTF)
- Online Labs
- Servers
- Explore tools such as Shodan, Censys Search, and ZoomEye for discovering vulnerabilities and improving security.
- Access databases like NIST NVD and MITRE CVE for identifying and cataloging cybersecurity vulnerabilities.
- Discover exploits through platforms like Exploit-DB and Rapid7 DB to enhance your offensive security skills.
- Title
- Craft a concise title that encapsulates the issue and its impact.
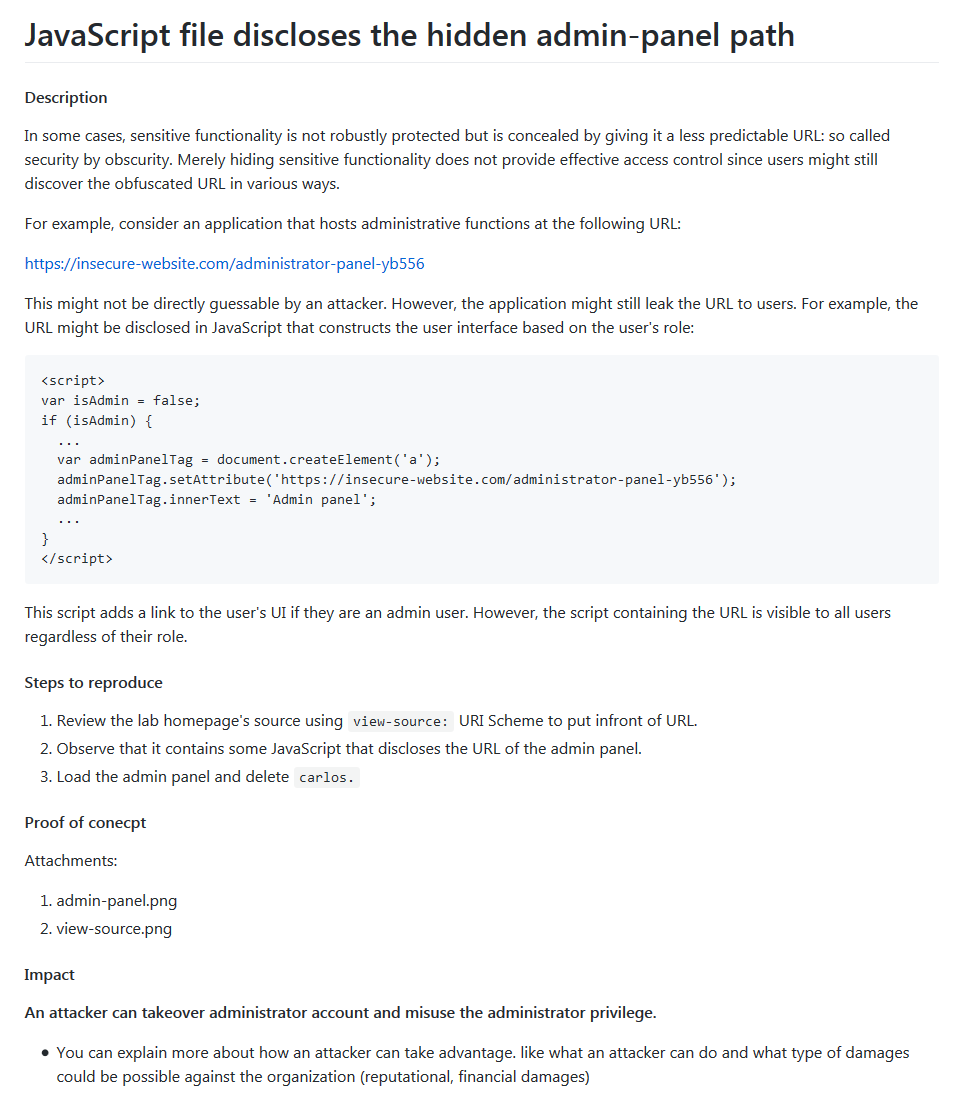
- Description
- Provide detailed information about the vulnerability, including paths, endpoints, and relevant HTTP requests.
- Steps to Reproduce
- Clearly outline the steps to replicate the bug for verification purposes.
- Proof of Concept
- Include visual aids such as screenshots or demonstration videos.
- Impact
- Describe the real-life consequences of the vulnerability in alignment with the organization's objectives.
- Start bug bounty hunting as a part-time endeavor initially, maintaining multiple income streams for stability.
- Stay updated by following relevant resources and engaging with the cybersecurity community.
- View bug bounty hunting as a means to enhance skills rather than solely for monetary gain.
- Develop unique methodologies and avoid over-reliance on automation tools.
- Consider the severity and context of a vulnerability when assessing its impact.
- Network with peers and share knowledge within the community.
- Be proactive and supportive within the bug bounty community.
Feel free to contribute to this roadmap and happy bug hunting!