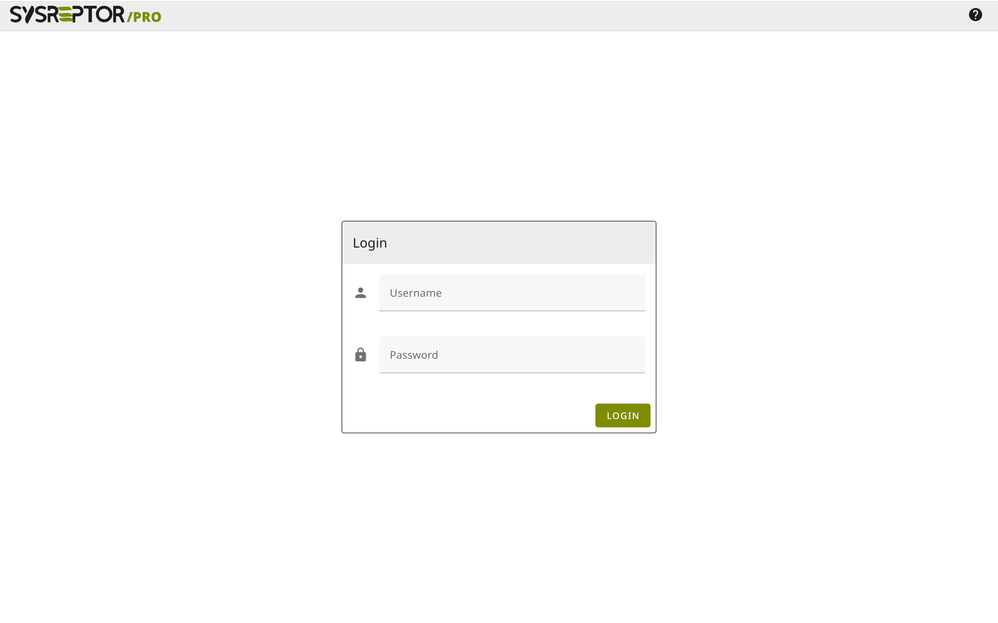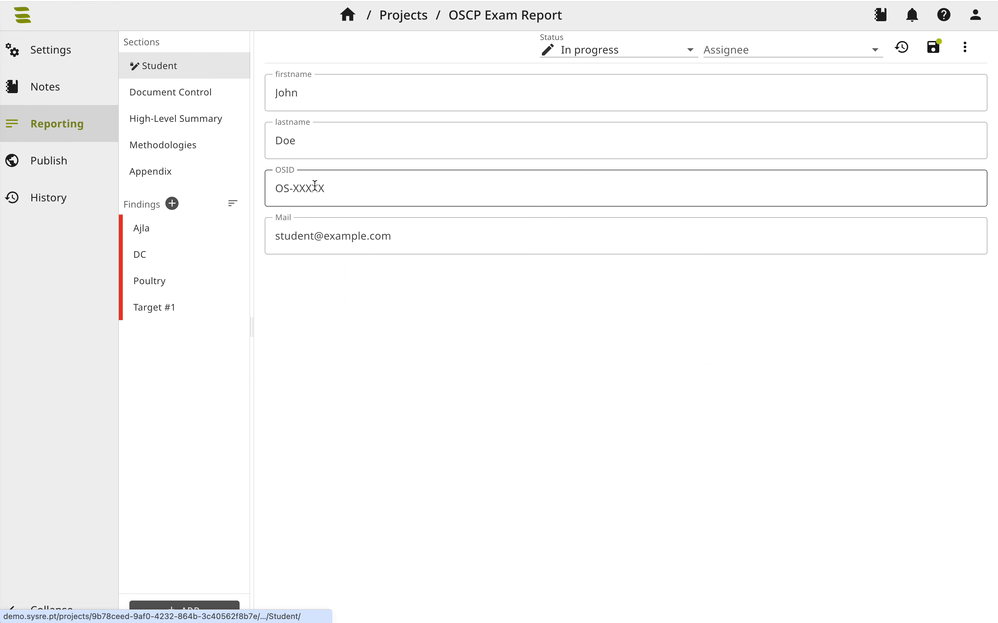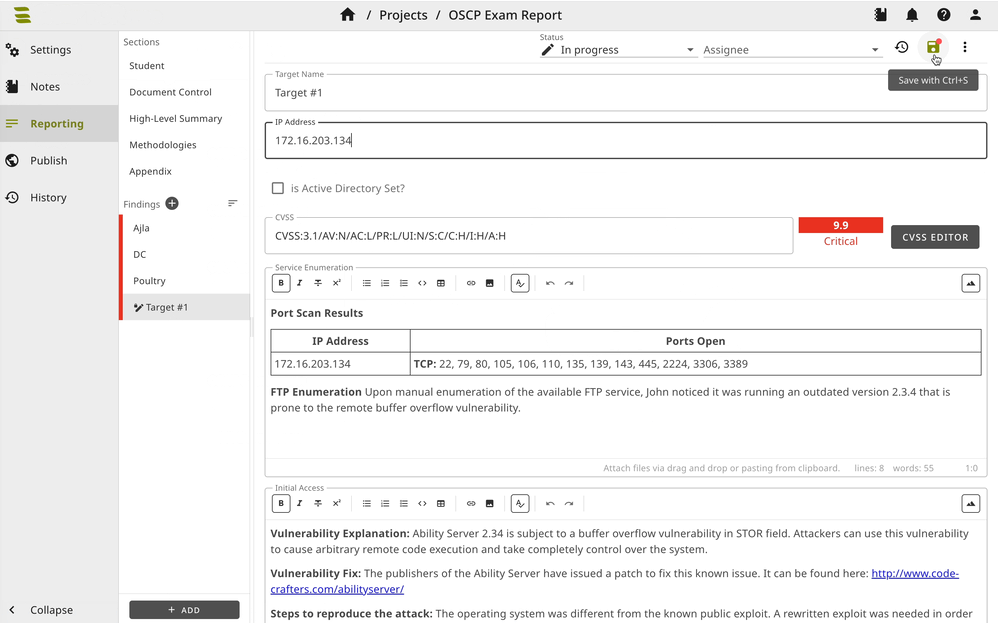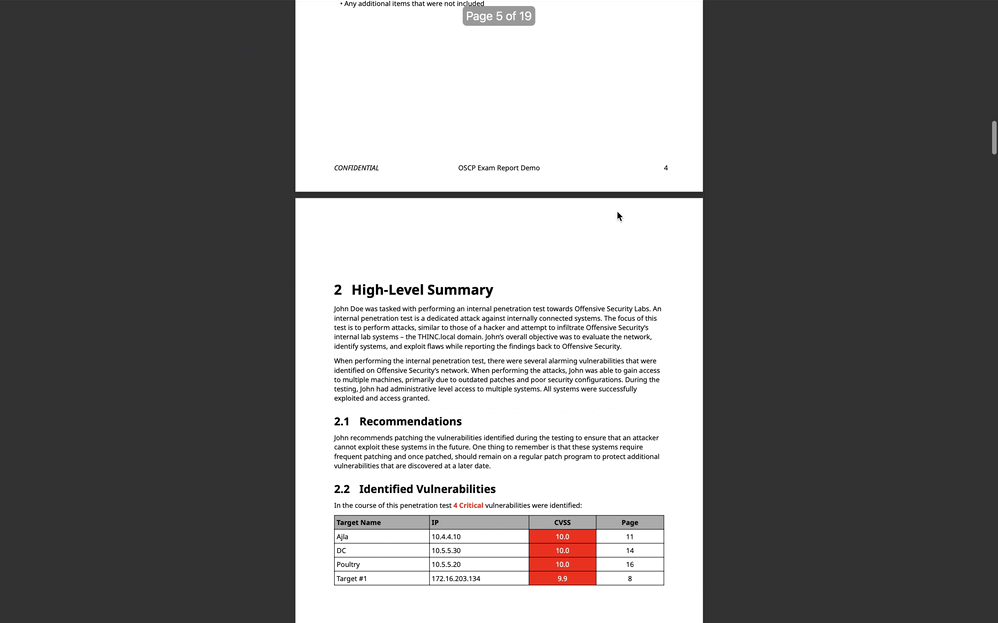
This is our OffSec reporting repository showcasing OffSec reports created with SysReptor. Write your OffSec OSCP, OSWP, OSEP, OSWA, OSWE, OSED, OSMR, OSEE, OSDA reports.
Feedback is very welcome! ❤️
🚀 # here (it's free)
Already have an account? Login here.
- Install SysReptor
- Import all OffSec Designs:
cd sysreptor/deploy
url="https://docs.sysreptor.com/assets/offsec-designs.tar.gz"
curl -s "$url" | docker compose exec --no-TTY app python3 manage.py importdemodata --type=design💡 Have a look at our documentation.
PS: Are you missing a template, have feedback or any other questions?
Let us know! Open an issue or mail us and are happy to help you.
Happy Reporting! 🦖
💲 Free
📝 Write in markdown
⚙️ Render to PDF
🛡️ OSCP, OSWP, OSEP, OSWA, OSWE, OSED, OSMR, OSEE, OSDA
🚀 Fully customizable
👌 No local software troubleshooting
*The cover pages are based on noraj's great OSCP LaTeX templates. The structure follows the official OffSec reports (with kind permission by OffSec).
| Exam acronym | Exam name | Lab name | Course designation |
|---|---|---|---|
| OSCP | Offensive Security Certified Professional | PWK | Penetration Testing with Kali Linux |
| OSWP | Offensive Security Wireless Professional | WNA | Offensive Security Wireless Attacks |
| OSEP | Offensive Security Experienced Penetration Tester | ETBD | Evasion Techniques and Breaching Defenses |
| OSWA | Offensive Security Web Assessor | WAKL | Web Attacks with Kali Linux |
| OSWE | Offensive Security Web Expert | AWAE | Advanced Web Attacks and Exploitation |
| OSED | Offensive Security Exploit Developer | WUMED | Windows User Mode Exploit Development |
| OSMR | Offensive Security macOS Researcher | MCB | macOS Control Bypasses |
| OSEE | Offensive Security Exploitation Expert | AWE | Advanced Windows Exploitation |
| OSDA | Offensive Security Defense Analyst | SODA | Security Operations and Defensive Analysis |