-
Notifications
You must be signed in to change notification settings - Fork 1
Trustmark Framework Background and Basic Concepts
This page is part of the TPAT User Guide.
The Georgia Tech Research Institute (GTRI) began developing the trustmark framework in 2013 under an NSTIC pilot grant from the National Institute for Standards and Technology (NIST). In the years since then, we have made substantial progress in developing the framework and conducting demonstrations and pilot projects with it. This page describes the basic motivation for the trustmark framework and also introduces its basic concepts.
Information Sharing & Safeguarding (IS&S) is widely recognized as a fundamental need of the public safety (PS) community. The community’s IS&S requirements are substantial and increasing, as the community works to respond effectively to a wide range of challenging, multi-agency events: opioid overdoses, school shooting incidents, large-scale natural disasters, etc. Federated Identity, Credential, and Access Management (Federated ICAM) is widely recognized as a critical capability that can help to enable PS IS&S across agency and jurisdictional boundaries, down to the level of sharing information with individual users in accordance with appropriate access control rules.
Before sensitive information can flow from one PS agency to another, and down to specific users within those agencies, there must exist a sufficient level of trust between the agencies. These trust relationships are usually based on a set of detailed questions that agencies must answer about the information being shared and about each other. For example:
-
What trust and interoperability policies and rules pertain to the type(s) of information being shared, with respect to topics such as security, privacy, identity vetting, authentication, identity attributes, etc.?
-
Does each agency implement these required policies as appropriate?
-
Does each agency implement IT systems that can communicate with partner agencies’ systems in a manner that is secure and interoperable, with respect to the agreed-upon Federated ICAM and information sharing protocol(s)?
Managing these trust relationships rigorously and efficiently is a daunting challenge for PS agencies. The trustmark framework enables agencies to take a structured approach to trust management from a unified perspective across all of their IS&S use cases and all their information sharing partners. In the absence of such a structured framework, agencies would tend to adopt ad hoc trust management strategies, which are inherently tactical (i.e., non-strategic), non-reusable, brittle (i.e., non-agile), and expensive to maintain at scale.
At a high level, the trustmark framework aims to make IS&S and Federated ICAM trust criteria transparent and explicit, so that all parties to a trusted information sharing transaction can understand exactly what criteria must be satisfied for trust and interoperability to exist, as well as what assessment steps must be completed — through either a self-assessment process or a more rigorous third-party assessment — to demonstrate satisfaction of those requirements. The framework also embraces and encourages componentization and modularity around trust requirements, to promote reusability of assessment results and therefore reduce costs. Finally, the trustmark framework leverages machine-readability of artifacts to promote automation and scalability.
The trustmark framework includes five key components:
- Trustmark Framework Functional Model — The figure below depicts the trustmark framework functional model, which defines the types of actors and machine-readable artifacts that comprise the framework. These include trustmarks, trustmark definitions (TDs), trust interoperability profiles (TIPs), trustmark defining organizations (TDOs), trustmark providers (TPs), trustmark recipients (TRs), and trustmark relying parties (TRPs).
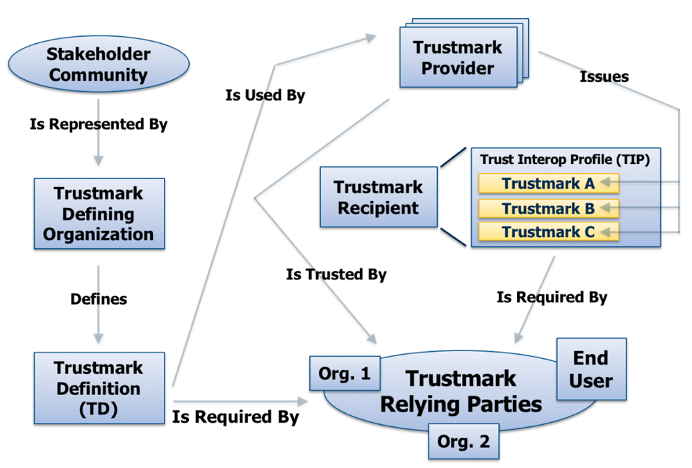
-
Trustmark Framework Technical Specification (TFTS) — The TFTS is a normative document that formally defines the trustmark framework, including technical artifact structures and rules for encoding those artifacts. The TFTS provides a foundation for wide-scale implementation of the framework.
-
Library of Trustmark Framework Policy Artifacts — There exists a large and growing library of trustmark framework artifacts that faithfully represent many prominent policies and technical standards with direct applicability to the PS community’s Federated ICAM and IS&S trust management challenges. Prominent PS policies and standards that are already represented as trustmark framework artifacts include NIST Special Publication 800-53 r4, NIST Special Publication 800-63, the FBI Criminal Justice Information Services (CJIS) Security Policy, and others.
-
Trustmark Legal Framework — The trustmark framework includes a pragmatic legal framework that was modeled after the well-understood and widely adopted public key infrastructure (PKI) legal framework. This enables trustmarks to be issued and relied upon for trusted information sharing transactions by allowing transaction participants to precisely understand the guarantees, liabilities, and risks inherent in their use of trustmarks.
-
Trustmark Framework Software Tools — One of the trustmark framework's core tenets is that standardized, machine-readable artifacts promote automation and scalability of trust management. The trustmark framework therefore depends on a rich suite of software tools to enable automation and scalable use of each major trustmark framework use case. The following software tools are under development:
-
Trust Policy Authoring Tool (TPAT) — The TPAT can be used to develop and publish trustmark definitions (TDs) and trust interoperability profiles (TIPs) that represent an agency’s trust policies for info sharing with its partners.
-
Trustmark Assessment Tool (TAT) — The TAT can be used to perform assessments and issue and publish trustmarks based on those assessments.
-
Trustmark Binding Registry (TBR) — The TBR enables published trustmarks to be bound to live systems such as SAML endpoints, so that other systems can perform automated lookups and make automated trust decisions.
-
Trustmark Relying Party Tool (TRPT) — The TRPT is the software that actually does those automated lookups and makes those trust decisions about the agencies and systems that have trustmarks.
-
Previous: Welcome | Next: Deploying a TPAT
This content was developed by the Georgia Tech Research Institute under the Trustmark Initiative.