-
-
Notifications
You must be signed in to change notification settings - Fork 5.7k
New issue
Have a question about this project? # for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “#”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? # to your account
Both repository/contents API endpoints return 500 when a file contains a '%' sign #22843
Labels
Comments
lunny
pushed a commit
that referenced
this issue
Feb 12, 2023
Fixes: #22843 ### Cause: https://github.com/go-gitea/gitea/blob/affdd40296960a08a4223330ccbd1fb88c96ea1a/services/repository/files/content.go#L161 Previously, we did not escape the **"%"** that might be in "treePath" when call "url.parse()". 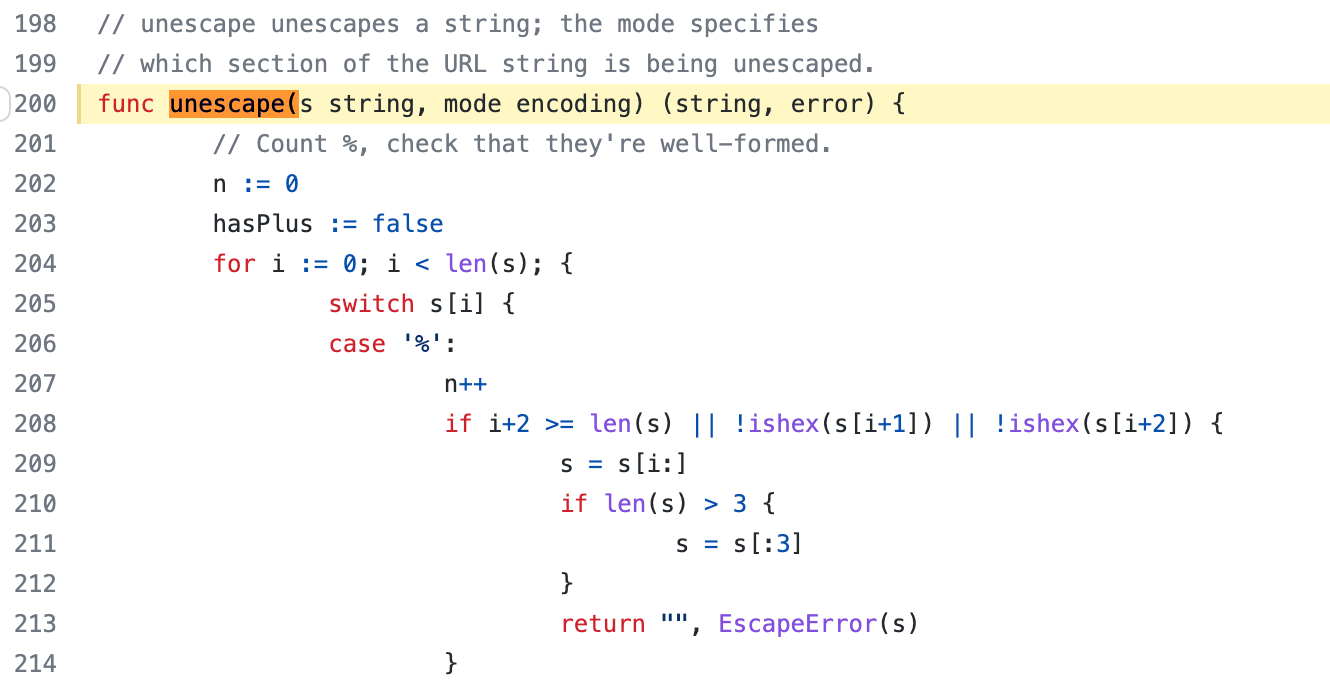 This function will check whether "%" is the beginning of an escape character. Obviously, the "%" in the example (hello%mother.txt) is not that. So, the function will return a error. ### Solution: We can escape "treePath" by call "url.PathEscape()" function firstly. ### Screenshot: 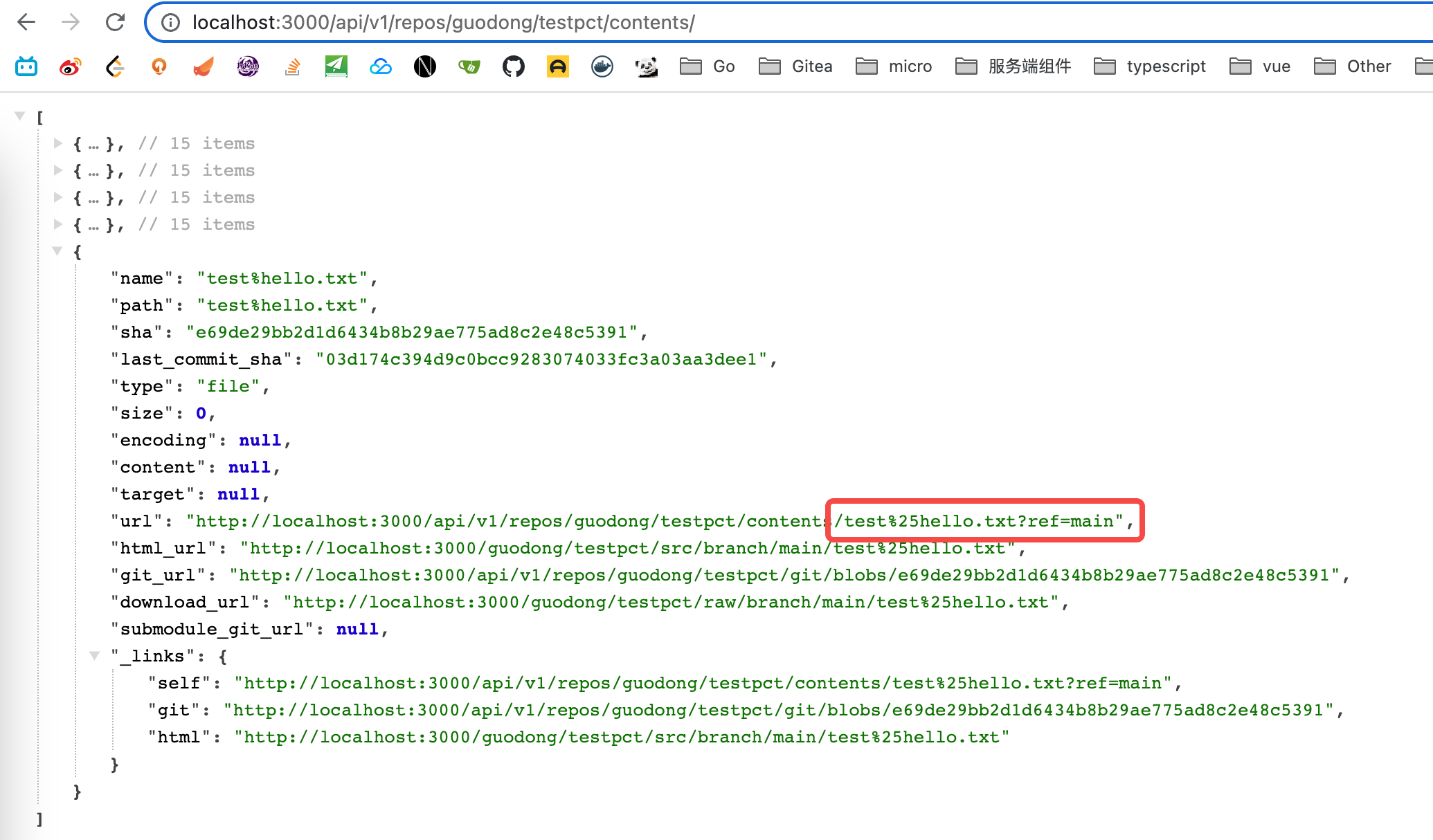 --------- Signed-off-by: Andrew Thornton <art27@cantab.net> Co-authored-by: Andrew Thornton <art27@cantab.net>
yardenshoham
pushed a commit
to yardenshoham/gitea
that referenced
this issue
Feb 12, 2023
Fixes: go-gitea#22843 ### Cause: https://github.com/go-gitea/gitea/blob/affdd40296960a08a4223330ccbd1fb88c96ea1a/services/repository/files/content.go#L161 Previously, we did not escape the **"%"** that might be in "treePath" when call "url.parse()".  This function will check whether "%" is the beginning of an escape character. Obviously, the "%" in the example (hello%mother.txt) is not that. So, the function will return a error. ### Solution: We can escape "treePath" by call "url.PathEscape()" function firstly. ### Screenshot:  --------- Signed-off-by: Andrew Thornton <art27@cantab.net> Co-authored-by: Andrew Thornton <art27@cantab.net>
zeripath
added a commit
that referenced
this issue
Feb 12, 2023
Backport #22850 Fixes: #22843 ### Cause: https://github.com/go-gitea/gitea/blob/affdd40296960a08a4223330ccbd1fb88c96ea1a/services/repository/files/content.go#L161 Previously, we did not escape the **"%"** that might be in "treePath" when call "url.parse()".  This function will check whether "%" is the beginning of an escape character. Obviously, the "%" in the example (hello%mother.txt) is not that. So, the function will return a error. ### Solution: We can escape "treePath" by call "url.PathEscape()" function firstly. ### Screenshot:  Signed-off-by: Andrew Thornton <art27@cantab.net> Co-authored-by: sillyguodong <33891828+sillyguodong@users.noreply.github.com> Co-authored-by: Andrew Thornton <art27@cantab.net>
# for free
to subscribe to this conversation on GitHub.
Already have an account?
#.
Description
This bug can be found in both GET endpoints:
repository/contentsas well asrepository/contents/{filepath}One can reproduce this bug fairly easily:
testpct.hello%mother.txt)http://MYHOST/api/v1/repos/USERNAME/testpct/contents{ "message": "", "url": "http://localhost:3000/api/swagger" }folder.http://MYHOST/api/v1/repos/USERNAME/testpct/contents/folderFor the record, I am well aware that having special characters in file names is bad and, no, changing these file names is not possible. :)
Gitea Version
1.17.0, 1.18.3
Can you reproduce the bug on the Gitea demo site?
Yes
Log Gist
https://gist.github.com/SolarBear/66fe09b5817c1aab74fa5292bebc894d
Screenshots
No response
Git Version
No response
Operating System
Windows 10
How are you running Gitea?
Database
SQLite
The text was updated successfully, but these errors were encountered: