-
-
Notifications
You must be signed in to change notification settings - Fork 422
FS_Process_Files
The directory files exists as a sub-directory in each process directory.
The files directory contains three sub-directories named handles, modules and vads. Please see the table below for information about each individual sub-directory.
| Directory | Description |
|---|---|
files/handles |
Files reconstructed from open process file handles. Files may be reconstructed using techniques for Image, Cache and Data reconstruction. |
files/modules |
Reconstructed modules such as .exe, .dll and .sys files from memory fragments. Files are generated by parsing process PEB and module headers |
files/vads |
Files reconstructed from virtual address descriptors (VADs). Files may be reconstructed using techniques for Image, Cache and Data reconstruction. |
Please note that files in the files directory are best-effort reconstructed files. The files may not match the real file system files since all fragments may not reside in memory and as such will be zero-padded. Even if most memory is available certain parts, such as the import table, of PE images that changed in runtime will not be re-constructed perfectly.
Files in the files/handles and files/vads directories are read-only. Files in the files/modules directory are writable if a write-capable memory acquisition device is used. Please note that physical memory backing modules are normally shared between all processes and that any writes may affect all processes with the module being written into.
The example below shows the files in the files/handles sub-directory of the svchost.exe process and files in the files/modules sub-directory of the explorer.exe process. The files/handles directory contains files partially best-effort reconstructed from open process file handles. The files/modules directory contains best-effort, from usermode, reconstructed .exe and .dll PE modules. Missing information will be zero-padded.
Recovered files are likely to have missing information and may be somewhat corrupt and may not be executable or readable as such. They may however be useful for other operations, such as looking at properties, reversing, debugging and scanning for known strings and signatures.
Note that the event logs in the example below may sometimes be opened as-is, without further repair, by the event viewer if copied to a separate directory first. Event viewer will fail open directly from the files/handles sub-directory since it's unable to create a temp file.
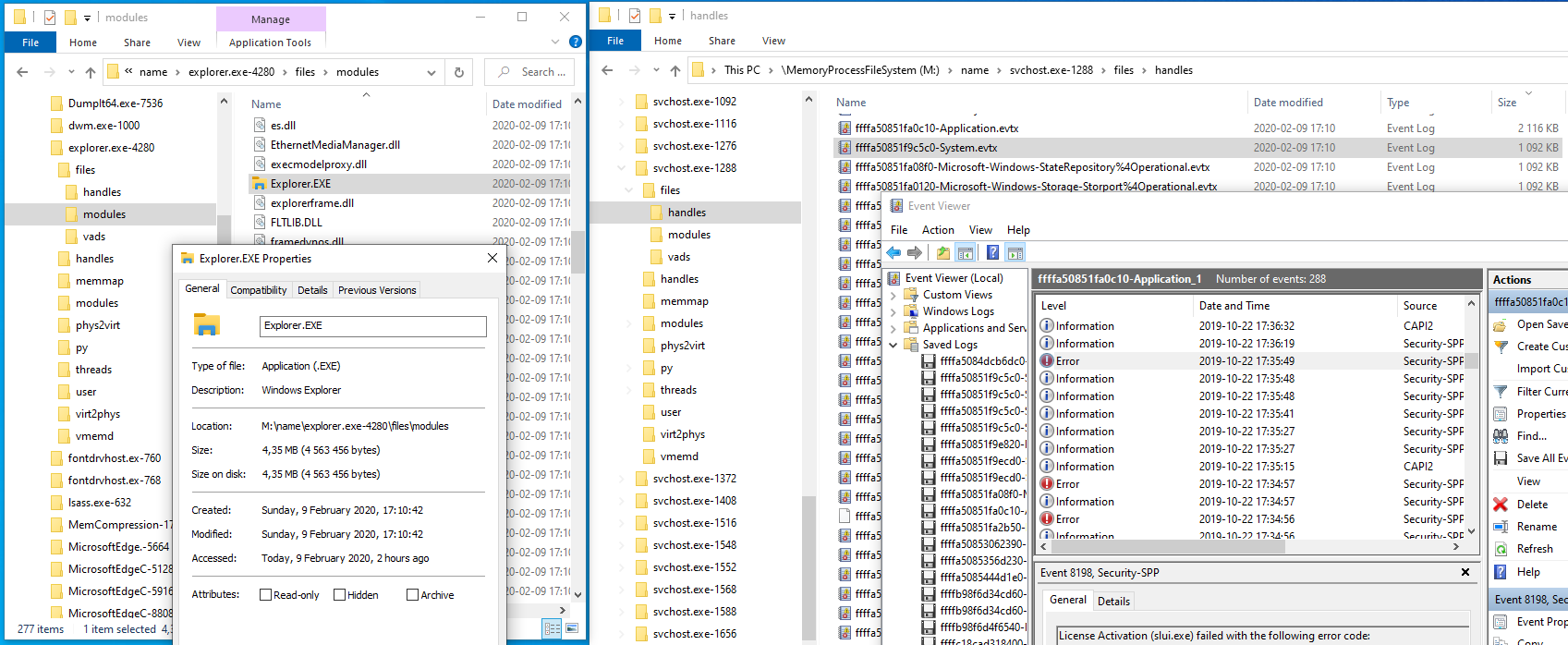
The files sub-directory is implemented as two separate built-in native C-code plugins. The plugin source is located in the files modules/m_proc_file_handles_vads.c and modules/m_proc_file_modules.c in the vmm project.
Sponsor PCILeech and MemProcFS:
PCILeech and MemProcFS is free and open source!
I put a lot of time and energy into PCILeech and MemProcFS and related research to make this happen. Some aspects of the projects relate to hardware and I put quite some money into my projects and related research. If you think PCILeech and/or MemProcFS are awesome tools and/or if you had a use for them it's now possible to contribute by becoming a sponsor!
If you like what I've created with PCIleech and MemProcFS with regards to DMA, Memory Analysis and Memory Forensics and would like to give something back to support future development please consider becoming a sponsor at: https://github.com/sponsors/ufrisk
Thank You 💖