-
-
Notifications
You must be signed in to change notification settings - Fork 422
FS_Process_ProcStruct
The directory py/procstruct exists as a sub-directory in each process directory if the process is a Windows process.
The directory and its contents are implemented as a Python module. Python functionality must work for the py/procstruct directory to be visible. Please find it in the plugins/pym_procstruct relative to MemProcFS.exe.
The directory files contains the memory of the EPROCESS and PEB data structures related to the process being analyzed. If a 32-bit WoW64 process is analyzed files containing the memory of the 32-bit PEB will appear as PEB32. Both binary and test representations of memory are displayed.
The text files are always read-only. The binary files are writable if a write-capable memory acquisition device is used.
The example below shows the EPROCESS, PEB and PEB32 of the 32-bit OneDrive.exe process. The EPROCESS is viewed in a hex editor while the 32-bit PEB32 is viewed in Notepad.
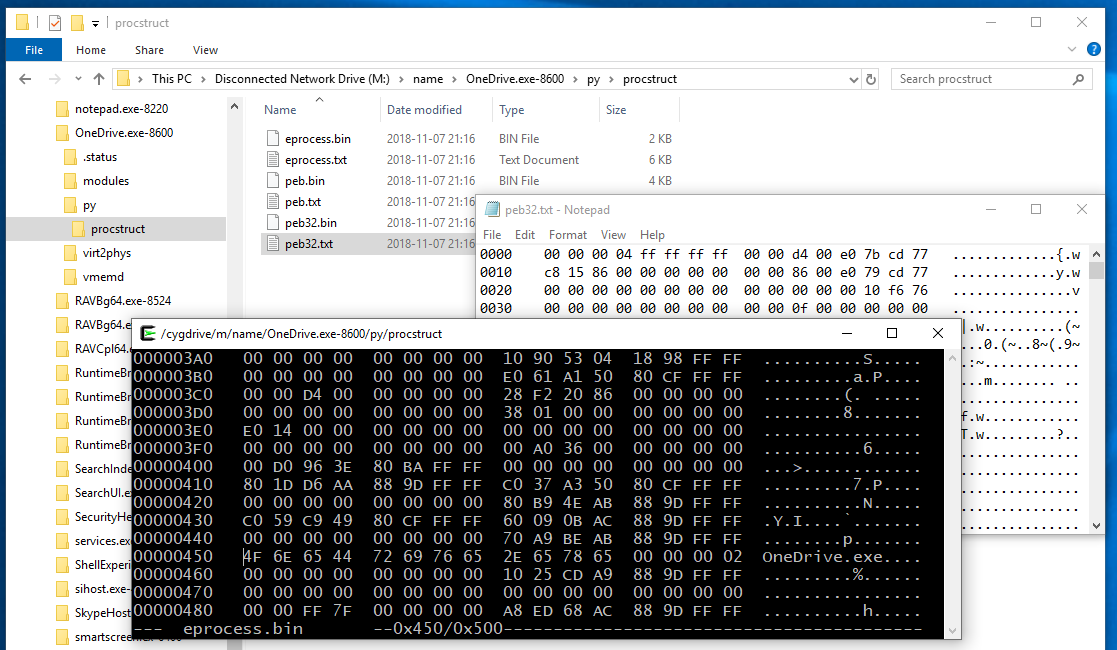
The py/procstruct sub-directory is implemented as a python module. The module is located in plugins/pym_procstruct relative to MemProcFS.exe. The Python source code is well documented and make heavy use of the VmmPy library. For more information about Python modules check out the Python Modules wiki topic.
Sponsor PCILeech and MemProcFS:
PCILeech and MemProcFS is free and open source!
I put a lot of time and energy into PCILeech and MemProcFS and related research to make this happen. Some aspects of the projects relate to hardware and I put quite some money into my projects and related research. If you think PCILeech and/or MemProcFS are awesome tools and/or if you had a use for them it's now possible to contribute by becoming a sponsor!
If you like what I've created with PCIleech and MemProcFS with regards to DMA, Memory Analysis and Memory Forensics and would like to give something back to support future development please consider becoming a sponsor at: https://github.com/sponsors/ufrisk
Thank You 💖